
Discover The SEED
The device that turns any computer into a secure workstation.
Turn any computer
into a secure workstation.
One simple action is all it takes: plug the SEED in via USB. Restart.
Your machine then boots directly into the professional environment contained within the SEED,
without touching the local system.

Plug in the SEED
The SEED is connected to the computer
The device becomes the primary boot source, ready to load the secure environment.
Restart
The user
restarts
The computer completely ignores the internal drive and loads the system contained in The SEED, deployed by the company.
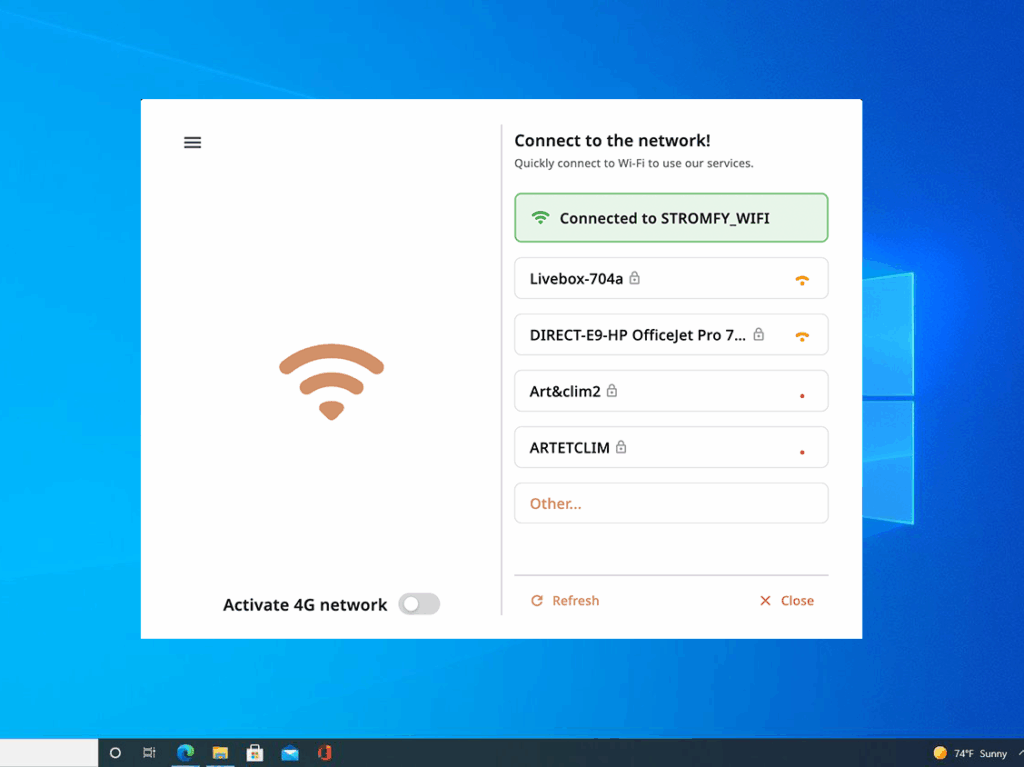
Immediate secure connection
Nothing to configure.
The SEED automatically connects via Wi-Fi or 4G, establishes a secure tunnel to your servers, applies company policies and synchronises data.
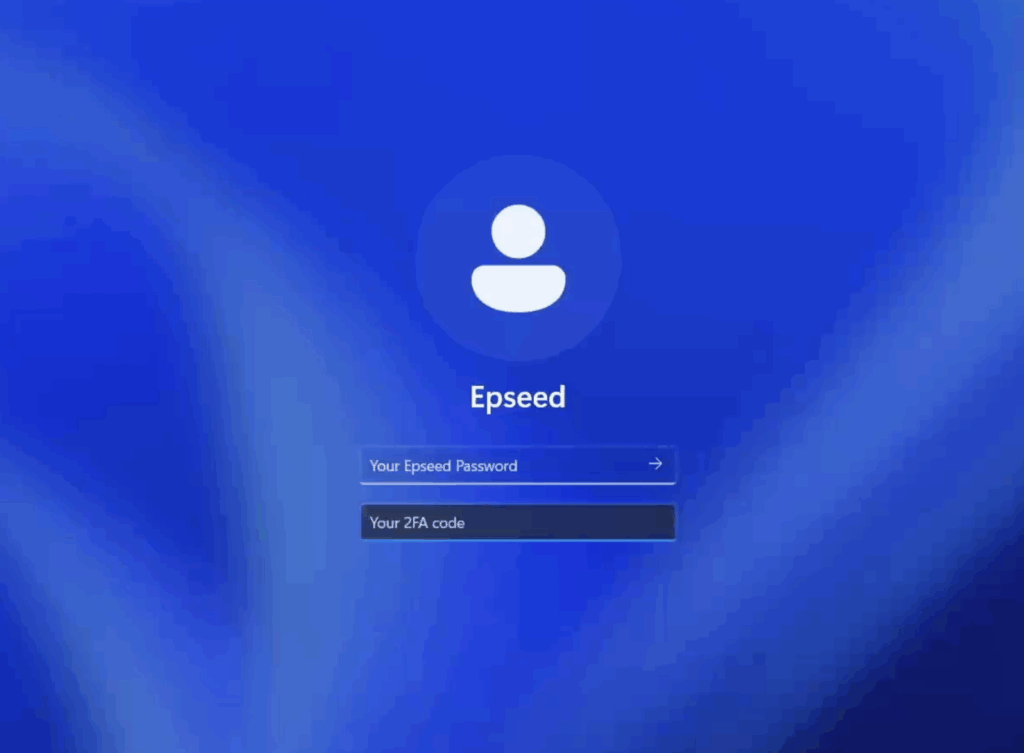
Environment ready
Log in with company credentials
The system runs in memory, without mounting the host disk. No data passes through the local computer.
Where everything changes
A new way to access a workstation: no installation, no dedicated computer, no exposure of the local system.
The SEED removes everything that complicates modern work — and keeps only what matters: efficiency, security and freedom.

No software to deploy
The SEED contains your entire system. Nothing to install, nothing to maintain on user machines.
The same workstation, everywhere
Same environment, same files, same performance — whatever computer is used.
Zero footprint on the host
The local disk is never used. No trace, no risk, no possible contamination.
Centralised administration
Images, policies, access rights and updates: everything is managed from a single interface across the entire fleet.
Unified management of the SEED fleet
The SEED is not just a box: it's a complete ecosystem. From a unified console, your teams deploy, configure, monitor, and secure the entire fleet—without ever touching employees' workstations.

Simplified deployment
Create and replicate your environments with ease
Prepare your Windows or Linux images, then replicate them onto each SEED using our dedicated tool, with no complex configuration.
Simplified user management
Assignment, permissions, onboarding: everything is seamless

Assign a device, control access, apply policies…
or connect The SEED to your existing directory (AD, LDAP, Azure AD).
Real-time monitoring

The SEED combines hardware encryption, strong authentication and remote control to ensure complete security, even when on the move.
Remote actions
(total security)

A comprehensive administration interface allows companies to manage the entire SEED fleet from a single console.
Seed Pro
Demander un devis dès maintenant !

